4.5. Traffic analysis
A certain amount of information can be extracted indirectly from dataflow of packets leaving and entering a personal computer or, for that matter, a borderline cloud gateway. This can later be used in further analysis and cryptanalysis, possibly leading to as little as privacy breach, and as much as data capture in due course.
Co-location testing
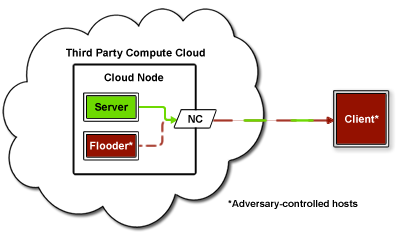
Just to show that it is possible to use traffic analysis as a starting point to launch a cyber-attack we shortly refer a co-residency test from : 1 . Refer to the following figure:
The attack leverages on the fact that two co-located VMs in fact share the same physical network interface (NIC). The client machine, located outside the cloud, initiates connection with the targeted server and at the same time sends initiation request to the flooder -- an attacker-owned machine, which, has been started in huge numbers in the cloud, thus increasing the probability of co-location with the server. On request, the flooder injects a specifically crafted communication into its network interface. If the flooder and the server use the same physical NIC, then the communication statistics (round-trip time, delay time) will be altered depending on the pattern of communications from the flooder, thus providing proof for co-location. This technique of side-channel attack is known as \(traffic\ watermarking\) and has been shown to be applicable in commercially available public cloud scenarios (see citation above).
Bates, A., Mood, B., Pletcher, J., Pruse, H., Valafar, M., Butler, K.: Detecting co-residency with active traffc analysis techniques
In: Pro-ceedings of the 2012 ACM Workshop on Cloud Computing Security Workshop. CCSW '12, New York, NY, USA, ACM (2012) 1-12. http://doi.acm.org/10.1145/2381913.2381915