
5.1. Introduction to data management
Despite of all the benefits of outsourcing data management, it should be emphasized that in such a case clients do not have any direct control over the systems that manage their data. Thus the following questions arises:
- How can the client trust that a cloud provider will not leak any sensitive information or itself use his data in inappropriate way?
- How the client can be sure that his data is still available in the cloud?
- How the client can be sure that his data has not been changed by the cloud servers?
- How the client can be sure that his data was successfully deleted from the cloud?
- How the client can be sure that the protocol used for saving the storage space (de-duplication) is secure and does not leak any information about the data stored.
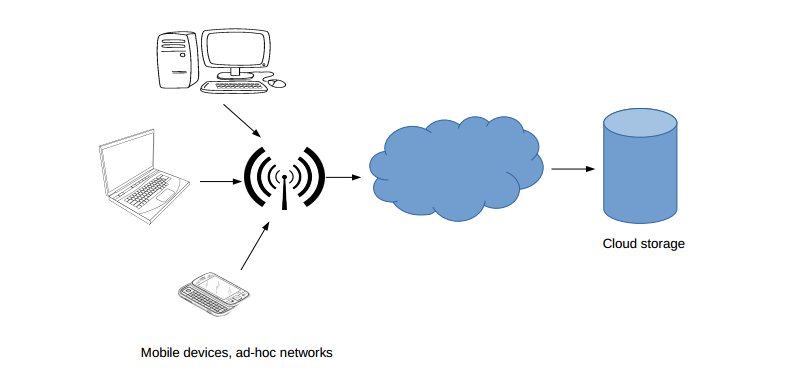
Fig. 5.1/1: Example architecture
Note
Designing solutions for the security concerns should take into account that sometimes the client in the cloud architecture might be a small device (e.g. a cell-phone) with limited resources in the field of communication facilities, memory, CPU and battery power. Thus:
- the volume of data exchanged between the user and the cloud and
- the local computation and memory usage
Projekt Cloud Computing – nowe technologie w ofercie dydaktycznej Politechniki Wrocławskiej (UDA.POKL.04.03.00-00-135/12)jest realizowany w ramach Programu Operacyjnego Kapitał Ludzki, Priorytet IV. Szkolnictwo wyższe i nauka, Działanie 4.3. Wzmocnienie potencjału dydaktycznego uczelni w obszarach kluczowych w kontekście celów Strategii Europa 2020, współfinansowanego ze środków Europejskiego Funduszu Społecznego i budżetu Państwa