
5.4.2. Vanish - time-based deletion
Permanently deleting data after storage time passes:
- even if an attacker can retroactively obtain a pristine copy of that data and any relevant persistent cryptographic keys and passphrases from before the timeout,
- without the use of any explicit delete action by the user,
- without needing to modify any of the stored or archived copies of that data,
- without the use of secure hardware,
- without relying on the introduction of any new external services that would need to be deployed.
Vanish features
Vanish utilizes P2P network in order to store key shares. The idea of time-based deletion relies on keys that are valid only in a given period or are deleted after given time.
- pick at random data key \(K\), \(C:=Enc_K (D)\)
- split the data key \(K\) into \(N\) shares (cf. Adi Shamir, How to share a secret : 2 )
- pick at random access key \(L\) and use it as a seed for secure PRNG, using PRNG\((L)\) calculate \(N\) nodes, where each key share will be stored
- each key share is deleted after given time (8 hours default for Vanish based on Vuze DHT), if key is still needed user has to reupload it
- cryptogram \(C\) is stored in cloud storage
One can notice that after all key shares are deleted, data \(D\) is not accessible.
Vanish: performance
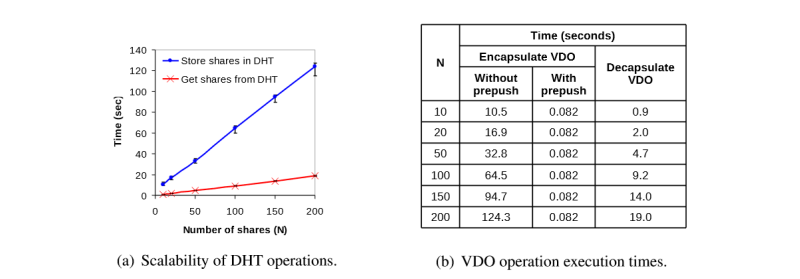
Fig. 5.4.2/1: Scalability of DHT
Picture Fig. 5.4.2/1 from : 1 , depicts scalability of DHT operations in author's implemented Vuze-based Vanish system. Based on experiments, the authors determine that for files under 100MB splitting key into shares and storing it in P2P network takes over 90% of the time overhead related to using Vanish, hence if Vanish Data Object is stored in the cloud and rarely accessed to, the overhead is not significant.
Vanish: summary
Data may be stored in Cloud storage in encrypted form, while key shares are stored either using Distributed Hash Tables as proposed by authors or in cloud itself (there should be no apparent connection between the data and key shares, hence it is strongly recommended to use different cloud storage provider for both purposes). Such approach allows to share data stored in cloud with different users at the cost of slight overhead, however after given time the key shares are deleted and if the data is not deleted by the storage provider it is inaccessible. Note that since key shares are distributed among different nodes there has to be some collusion between the nodes in order to retrieve the encryption key. Furthermore there is no connection between key shares and the data, hence the entity where the key shares are stored cannot learn where to find encrypted data.
Application
The application is available on http://vanish.cs.washington.edu/download.html .
Geambasu, R., Kohno, T., Levy, A., Levy, H.M.: Vanish: Increasing data privacy with self-destructing data.
In: Proc. of the 18th USENIX Security Symposium. (2009)
Shamir, A.: How to share a secret.
Commun. ACM 22(11) (1979) 612-613. http://doi.acm.org/10.1145/359168.359176