
8.1.1. Attacks on surfaces
The goals of the talk
- Examine attack surfaces in a cloud
- Learn about novel attacks on clouds
Securing a house
- Owner and user are often the same entity,
- Concerns of users:
- secure perimeter,
- check for intruders,
- secure assets.
Securing a hotel
- Owner and user are almost always different entities,
- Concerns of users:
- secure room against the bad guy in next room,
- protect room against the hotel owner.
Attack surface definition
A system’s attack surface is the subset of the system’s resources that an attacker can use in order to attack the system.
Clouds extend the attack surface
- users communicate with the cloud over a public (possibly insecure) communication network,
- the infrastructure is shared among multiple users.
Participants in cloud computing
A cloud computing scenario can be modelled using three classes of participants:
- service users,
- service instances,
- cloud provider.
Interaction in cloud computing
Every interaction in the cloud computing scenario can be adressed by two participants (e.g. user requesting a service or the service instance inquiring more CPU power from the cloud).
Attack in cloud computing
Similar, every attack can be detailed into a set of interactions within this 3-class model.
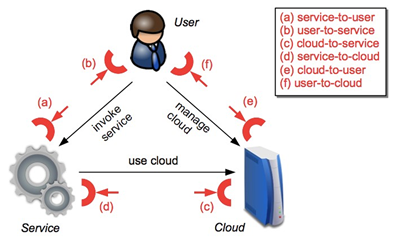
Fig. 8.1.1/1: Figure from : 1
a) SERVICE-to-USER
This is the common server-to-client interface, which includes (among others) the following attacks:
buffer overflow
SQL injection
privilege escalation
b) USER-to-SERVICE
The attack surface the service user provides to the service include attacks like:
SSL certificate spoofing
browser cache attacks
phishing attacks on mail clients
c) CLOUD-to-SERVICE
The cloud-to-service interface allows to perform attacks like:
resource exhaustion, i.e. popularly called Denial-of-Service attacks (DoS)
hypervisor attacks
d) SERVICE-to-CLOUD
This interface can be user to perform the following attacks:
- availability reduction (i.e. shut down service instances),
- privacy related attacks (scanning a service instance’s data in process),
- malicious inteferences (e.g. tampering data in process, injection of operations in services execution).
e) CLOUD-to-USER
This touch point does not really exist (there always exists a service between cloud and user). However, the cloud system must provide a way to control it, i.e. to allow to add and delete service instances. Attacks allowed by this interface are similar to point a).
f) USER-to-CLOUD
This last attack surface that includes phishing-like attacks to trigger a user into manipulating its cloud-provided services (e.g. present a faked usage bill of the cloud provider).

