
4.6.2. New assets, moving services to cloud
A standard, "old-way" of creating a company network is depicted in the following figure:
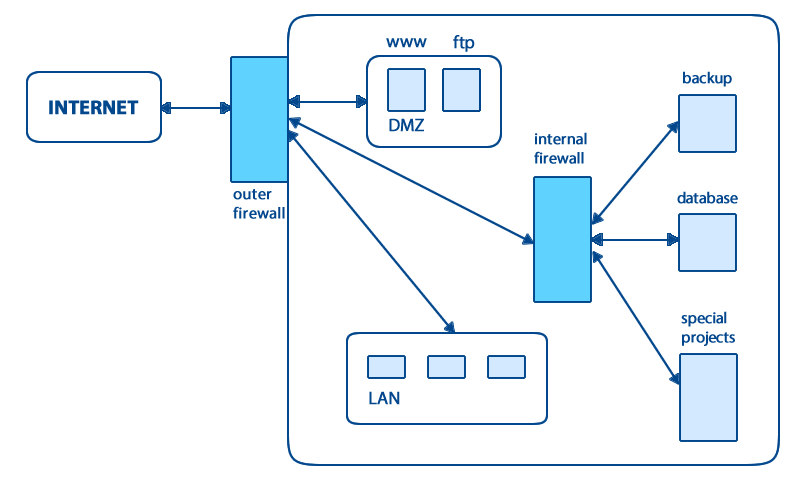
Fig. 4.6.2/1: An image of intranet
The company's network is guarded by a firewall facing the Internet and providing access to company's DMZ (demilitarized zone) servers. There WWW, FTP and such similar servers reside. Deeper inside, there usually is the company's LAN (local array network), where more sensitive data can be found, including mail server, and desktop computers. Additionally, hidden behind an additional firewall, there are high-security assets, such as database servers, backup storage and such like. Naturally, this is only a generic model and particular implementations may add to it with mode firewalls, servers and routers/switches.
Now consider moving towards a cloud-based solution. A natural step would be to move the web/ftp servers into cloud. Further, to leverage scalability and availability of the cloud, the company might deploy their servers into different clouds (in terms of geographical deployment, hence, possibly providers). As these used to be in DMZ anyway, with costs in mind, one might move the servers to a public cloud without much concern about security loss. On the other hand, sensitive services, such as backup and database is a completely different matter and in our example we move it to a private cloud. Finally, the company's desktops are connected to a SaaS-type cloud.
The network after re-modelling can look like this:
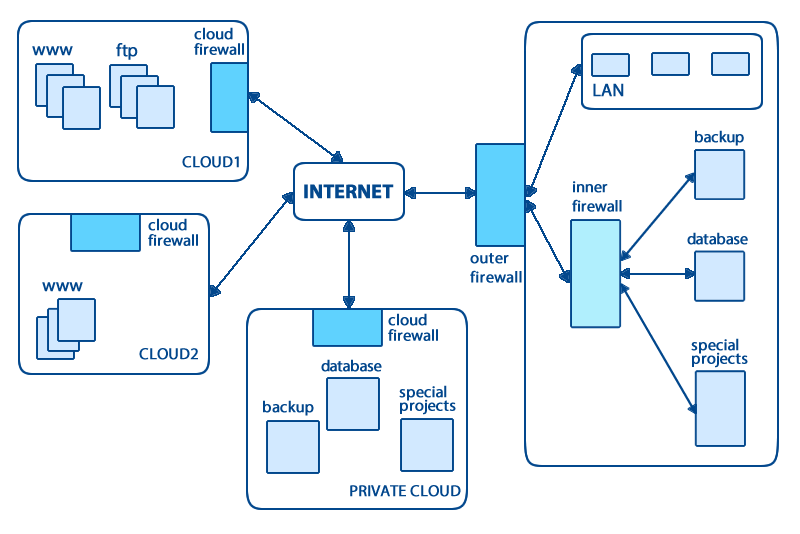
Fig.4.6.2/2: An image of cloud + firewalls + intranet
Moving to a cloud scenario consideration
Moving to a cloud scenario means that there is more firewalls to be managed, different traffic to be handled. Here are some things to consider regarding communication in the new setting:
- outer firewall: rules for letting traffic to/out of DMZ need to be changed, as well as these for desktop computers;
- inner firewall: secure tunnel to private cloud must be maintained;
- scaling up/down: as more WWW/FTP etc. servers are brought up or down depending on demand (see load balancing), the new virtual machines (VMs) need to be protected adequately.
- different providers: different providers may use different hardware firewalls and hence, the rules for one cloud may be not applicable in the other; this adds additional complexity to managing;